Authors
Robert Schultheis & Mary Sumner
Abstract
This study addresses the issue of risks and controls in end-user development. It analyzes two questions related to the design and construction of spreadsheet applications by end-users.
The first question focuses on the types of controls and the levels of risk associated with the applications themselves. The second question pertains to the extent to which control mechanisms are used to minimize the risk factors in development and use of spreadsheet data.
In other words, a basic auditing premise was tested: If managers are aware of the risk factors in the spreadsheets they develop, do they apply controls in design and implementation to assure that these risks are effectively controlled?
Sample
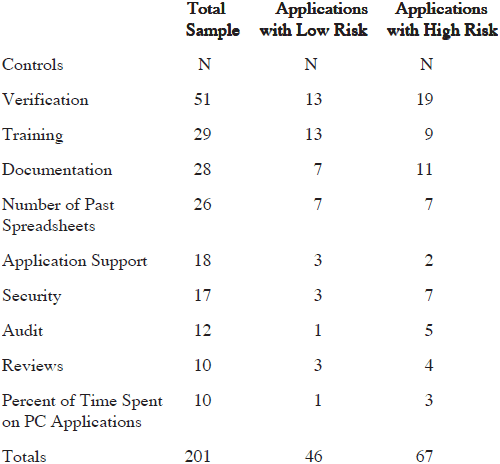
Our second research question was whether users apply controls consistent with the level of risk their applications pose. That is, do users apply a greater number of controls to high-risk as compared with low-risk applications?
The results indicate that users did apply more controls to the high-risk applications. Verification of logic, training, and documentation were the most commonly applied controls in the higher-risk applications.
Publication
1994, Journal of End User Computing, Volume 6, Issue 2, Spring, pages 11-18
Full article
The relationship of application risks to application controls
